
Thomas Fikentscher, Regional Director ANZ, CyberArk, chats to Government News about identity security and the changing threat landscape.

GN: What are we talking about when we refer to Identity Security and how has the threat landscape around it changed?
TF: Identity Security is a core set of capabilities that enables organisations to secure the access of human and machine identities to an organisation’s assets and data while enforcing least privilege and enabling Zero Trust.
With Identity Security, access is monitored on an ongoing basis with continuous identity threat detection so that the appropriate Identity Security controls such as session suspension and step-up authentication can be applied based on risk.
What are the biggest threats to Identity Security today?
The CyberArk 2022 Identity Security Threat Landscape Report identifies how the rise of human and machine identities – often running into the hundreds of thousands per organisation – has driven a build-up of identity-related cybersecurity “debt”, exposing organisations to greater cybersecurity risk.
Every major IT or digital initiative results in increasing interactions between people, applications, and processes, creating large numbers of digital identities. If these digital identities go unmanaged and unsecured, they can represent significant cybersecurity risks. This is especially the case in Australia – machine identities now outweigh human identities by a factor of 15x on an average, while the average staff member in Australia has greater than 33 digital identities.
Security professionals also agree that recent organisation-wide digital initiatives have come at the price of cybersecurity debt. Security programs and tools have grown but not kept pace with what organisations have put in place to drive operations and support growth.
This debt has arisen through not properly managing and securing access to sensitive data and assets, and a lack of Identity Security controls is driving up risk and creating consequences. It is compounded by the recent rise in geopolitical tensions, which have already had direct impact on critical infrastructure, highlighting the need for heightened awareness of the physical consequences of cyber attacks.
CyberArk’s recent Identity Security Threat Landscape report indicates that 52 per cent of respondents lacked security identity controls around cloud infrastructure, and 52 per cent of identities across business-critical apps are unprotected – how are these figures reflected in the government sector?
While it is difficult to get detailed reports from government agencies due to the protected nature of their systems and surrounding data, it is fair to assume the challenges faced by most government entities is similar to that of the private sector. Government decision-making is often slower and the degree of legacy infrastructure, higher. As such, a lot of administrative accounts, service accounts and general user accounts could possibly be unprotected.
Is Identity Security something government agencies should be concerned about, and if so, why?
The implications of an attack on our nation’s systems are far reaching – from disrupting the delivery of key services to impacting public safety. The damage from a cyber attack is no longer contained to the digital world as attacks can have grave consequences in the physical realm. The security of identities represents a top priority for critical infrastructure organisations in order to mitigate these risks.
Critical infrastructure is at a heightened risk with the growth in connectivity between Industrial Control Systems (ICS) within the operational technology environment and IT systems. For decades, these systems were isolated from IT systems and the Internet, but with increasing connectivity comes the increased risk of intrusion from malicious actors and malware.
Given today’s increasingly aggressive and dynamic threats, using technology to isolate these systems and limiting the attacker’s ability to move through the IT and OT systems and exploit remote control features is even more important.
What is the Zero Trust security model and how does it relate to Identity Security?
It is important to note that Zero Trust is not a solution or technology, but rather an approach to security based on the principle of “never trust, always verify.” This approach ensures that every user’s identity is verified, their devices are validated, and their access is intelligently limited to just what they need – and taken away when access privileges are no longer required.
As the embodiment of this model, Identity Security offers a set of technologies that is foundational to achieving Zero Trust. Identity Security helps enterprises secure human and machine identities including authenticating the identity, authorising it with the required permissions, and ensuring access for it to all corporate resources and environments. Identity Security is at the core of a zero-trust strategy, as it can help organisations empower workers and other stakeholders with secure access to apps and resources from any device they use.
How far down the road is the public sector an achieving a Zero Trust model, and what still needs to be done?
In many public sector areas, establishing a comprehensive Zero Trust model remains a challenging task and will require significant effort due to the sheer size and complexity of agencies involved.
Whilst most agencies have embarked on a roadmap that will eventually allow them to achieve Zero Trust, internal audits have time and again shown that the majority of them are just at the beginning and struggling to swiftly advance their security roadmaps.
Often, some fundamental and high-risk areas need to be addressed as priority before programs can be rolled out to a wider group of identities, and Tier 0 and Tier 1 accounts need to be brought under control before a broader sprawl of service accounts can be tackled. More effort and focus is needed to shorten the road towards a comprehensive Identity Security model.
What are the biggest weaknesses in current Zero Trust models and how can they be addressed?
A Zero Trust approach has proven to be an effective way for organisations to mitigate security risks. As most of the elements of a Zero Trust strategy have their roots in identity-based security solutions (multi-factor authentication, privileged access management), fortifying identity-based access controls must be one of the key focus areas for organisations to have better command and visibility of their corporate assets.
What is CyberArk doing to address Identity Security, and what can it offer the government sector in this respect?
Given the relentless drive for connectivity and digitization, it’s not surprising that attackers are going after a broader range of targets than we have ever seen, including nations’ energy grids, defence systems and even voting systems.
As such, organisations around the world, not just in Australia, need to proactively prepare themselves for attacks and avoid a wait-and-see approach. This means less emphasis on the forensics around attacks and much more focus on avoiding breaches with serious impact in the first place.
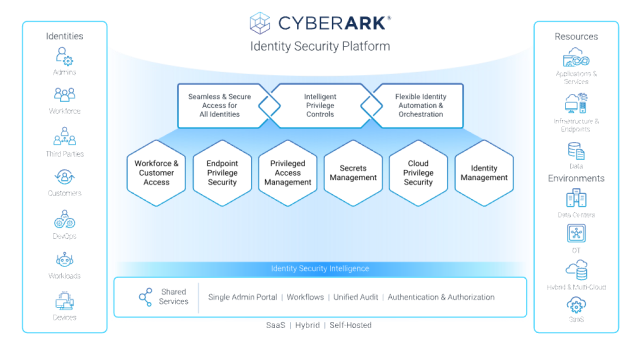
CyberArk’s Identity Security model is designed to provide seamless and secure access for all identities – human and non-human – to prevent attacks on any corporate resources or environments. This is why we offer a unified approach to Identity Security that is centered on intelligent privilege controls. Our solutions seamlessly secure access and flexibly automate the identity lifecycle with continuous threat detection and prevention.
Our unified Identity Security Platform enables secure access for any identity to any resource or environment from anywhere, using any device. Key features of the Identity Security platform include:
- Employee and customer access management: provides remote access for employees and external parties using general IDs, leveraging single sign-on and multi-factor authentication
- Endpoint Privilege Security: in addition to Windows and macOS, it now supports Linux, ensuring user security and operational efficiency by revoking local administrator privileges and granting least privileges
- Privileged Access Management: continuously detects and manages privileged accounts and credentials to detect anomalies in real time
- Secrets Management: enforces consistent access policies for all non-human credentials, including applications and machines, while maintaining access tracking and comprehensive auditing
- Cloud Privilege Security: continuously detects and remediates invisible, misconfigured, or unused privileges for access to any cloud platform, including AWS, Azure, Google Cloud Platform, etc., leveraging AI
Identity Management: detects user access and entitlements, and continuously assesses least privilege access and security risks.
How do you see the threat to Identity Security evolving in the future? What will future challenges be?
Today we are seeing threat actors, including nation states, criminal syndicates, ideologically-driven hacker groups and disgruntled insiders, continue to professionalise their operations. They also tend to collaborate frequently in order to be able to conduct large-scale and persistent attacks against significant targets that could even be entire countries. Geopolitical tensions, enhanced competition around energy and food supply as well as ‘hyper connectivity’ all point towards a higher volume and increased severity of cyber attacks.
One of the main challenges for government agencies would be to secure fundamental services that citizens need to rely on, such as access to energy, clean water, major food groups, essential healthcare and safe transportation.
Attacks on these critical infrastructure sectors could – in extreme cases – lead to casualties, which would be a major escalation when compared to a normal ransomware attack or the theft of minor data sets. Operational technologies, software-driven services and highly-automated processes should be areas of heightened focus.
Recent attacks on countries such as Costa Rica and Montenegro demonstrate the scale of the problem and will hopefully drive urgency in securing Australia’s most significant infrastructure assets.
Comment below to have your say on this story.
If you have a news story or tip-off, get in touch at editorial@governmentnews.com.au.
Sign up to the Government News newsletter