
Technological advances, a shifting geopolitical climate and cultural changes in the way we work and conduct business are opening new avenues for cyber criminals to steal information, disrupt systems and potentially threaten human safety.

The changing threat environment has seen the emergence of critical infrastructure systems as new targets, with recent attacks on oil infrastructure in the US and the world’s largest meat processing company JBS, causing disruption to supply chains, factory shutdowns, price spikes and panic buying.
Australia isn’t immune.
Locally, the Australian Cyber Security Centre says there’s been a 15 per cent increase in ransomware attacks, with around one in four cyber incidents reported between July 2020 and June 2021 affecting the nation’s critical infrastructure or essential services.
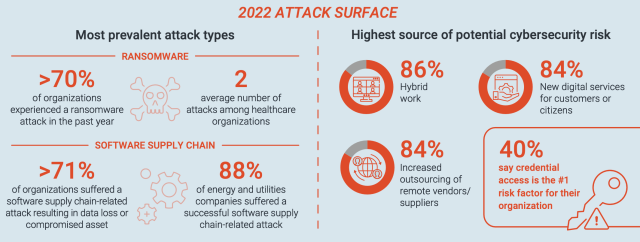
CyberArk’s 2022 Identity Security Threat Landscape report found a similar theme, with 70 per cent of organisations saying they had experienced a ransomware attack in the past twelve months, and almost 90 per cent of energy and utilities companies reporting a successful software supply chain-related attack in the last year.
Hybrid working patterns and an increase in outsourcing of vendors and suppliers were identified as driving the risks.
According to CyberArk’s Regional Director ANZ, Thomas Fikentscher, three key trends are driving the increasing risk to critical infrastructure:
- A convergence between information technology (IT) and operational technology (OT) networks – This has eliminated the “air gap” that traditionally separated the two environments, providing a pathway for threat actors to gain access to industrial control systems.
- Push to standards-based OT – Industrial control systems were once based on proprietary hardware and special-purpose software. In the current shift toward standards-based OT, many systems run on Linux-based commodity servers and leverage commercial-off-the-shelf (COTS) software, making them vulnerable to software supply chain attacks.
- Cloud adaptation – Critical infrastructure operators are increasingly adopting Software as a Service (SaaS), Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) solutions to accelerate the pace of innovation and support IoT programs like Smart Grid, Smart City and Smart Transportation systems. While essential to digital transformation, these cloud services also provide new ways for attackers to penetrate systems.
Strengthening critical infrastructure resilience
Australia has taken steps to respond to the changing cyber threat environment by widening the definition of critical infrastructure, mandating incident reporting and ramping up incidence response capability.
In 2018, the Australian Government introduced the Security of Critical Infrastructure Act, which sought to “manage the complex and evolving national security risks of sabotage, espionage and coercion posed by foreign involvement in Australia’s critical infrastructure.”
The Act originally covered only four sectors: electricity, water, gas and port infrastructure. However this was expanded last December to include 11 infrastructure sectors, including communications, data, defence, financial services, food, healthcare, higher education, research, transport, water and space technology. The legislation puts new requirements on agencies in these sectors to identify who owns and controls their IT assets; name outsourcers and off-shore providers; and specify the level to
which operators can access their networks, control systems, data holdings, security systems and corporate systems.
It also empowers the relevant Federal Minister to order critical infrastructure operators to take actions to reduce national security risks. For example, operators may be compelled to fix security loopholes and provide information about procurement and tenders. Australia has also joined the US, Canada, NZ and the UK in issuing a joint cybersecurity advisory, signalling a readiness to tackle issues such as “destructive malware, ransomware, DDoS attacks and cyber espionage” and providing collaborative mitigation strategies.
Moving to a Zero Trust model
CyberArk’s threat report also made the sobering discovery that 68 per cent of non-humans or bots are capable of accessing sensitive data.
This increasing threat has seen a trend towards the deployment of a Zero Trust model of information security, in which Australia’s critical infrastructure cybersecurity mandates and guidelines are grounded.
The Zero Trust model assumes that all digital identities – human or machine – are implicitly untrusted and must be authenticated and authorised regardless of their network or location.
Unlike traditional perimeter-based security models, which are becoming less effective as users increasingly operate outside the network and cloud uptake continues, Zero Trust is centred on identity.
It doesn’t assume implicit trust inside a corporate network, focusing instead on establishing and maintaining trust for every session.
Fikentscher says Zero Trust isn’t a single technology, but an approach involving different types of technologies including identity and access management, behavioural analytics, endpoint security, and network micro-segmentation.
Central to the model is the requirement for one consistent point of security control, which means a comprehensive Identity Security solution and strategy to encompass cloud-based IT and OT systems, as well as on-premises IT and OT systems.
In response, leading technology companies like CyberArk are offering solutions that secure all identities from end-to-end. Read more about how CyberArk is helping to address the Cyber Security Act here.
• CyberArk is a global company providing identity security solutions. For more information on CyberArk, go to www.cyberark.com.
Comment below to have your say on this story.
If you have a news story or tip-off, get in touch at editorial@governmentnews.com.au.
Sign up to the Government News newsletter